Every time you log into an app, shop online, fill out a form, or sign up for an email newsletter, you're sharing pieces of your digital self - and this already feels like a rather known fact - but you also share so much more. Even when you open a random website, hold your gaze a little longer on a post, or enter text on your phone's keyboard - even at these times you are sending information about yourself to 'data provider' companies. Your name and email might seem like harmless bits of information -- on their own -- but when paired with behavioral signals, such as your interests, hobbies, and job, it becomes possible to form a complete portrait of your persona. Google, Facebook (Meta), Apple, Unity - they all collect, form, and process a digital copy of you. A copy of your identity, a digital portrait painted by algorithms and neural networks, that is stored on tens, or perhaps hundreds of servers across the world - probably, without your knowledge of it.
Personally Identifiable Information, or PII, is any data that can identify you as an individual. All the things mentioned above mostly do not identify as PII - however once pieced together, they can all be formed into one. Think of it as your digital fingerprint. Sometimes a single piece of information (like your Social Security number or passport number) is enough to identify you. Other times, it takes several pieces combined-your name with your address and phone number-to create a more complete picture.
One might wonder - Why does protecting this information matter so much? Well, it's because when your PII falls into the wrong hands, the consequences can range from merely annoying to fully devastating. Identity theft, financial fraud, privacy violations-these aren't just abstract risks that you hear about on the news, but real-life problems affecting thousands or millions of people every year - unfortunately - they might be more near to you than you expect.
Beyond personal safety, PII protection builds the foundation of trust between you and the organizations you interact with. When a company safeguards your information properly, it shows respect for your privacy and your rights. This isn't just good business-it's becoming essential as people grow more aware of how their personal information is used and shared.
The PII chart
Of course, not all information poses the same level of risk. It is possible to map PII to a chart, with some information being much more sensitive than others. Sensitive PII is information that could - and will - cause significant harm if exposed, stolen, or leaked. Consider this example: your Social Security number can be used to open fraudulent accounts or file false tax returns. Credit/debit card numbers, bank account details, and loan information provide direct access to your money. Medical records reveal intimate details about your health conditions, medications, and treatments. Biometric data, like fingerprints or facial recognition patterns, is uniquely yours and cannot be changed if compromised. Driver's license numbers and passport information can be used to create fake IDs or commit fraud in your name.
At the other end of the chart lies non-sensitive PII. This includes information that identifies you but presents less risk if exposed. Your name, email address, and phone number fall into this category. Your work history, job title, and education background generally pose less risk on their own. Basic demographic information like age range or zip code provides some identifying details without revealing everything about you.
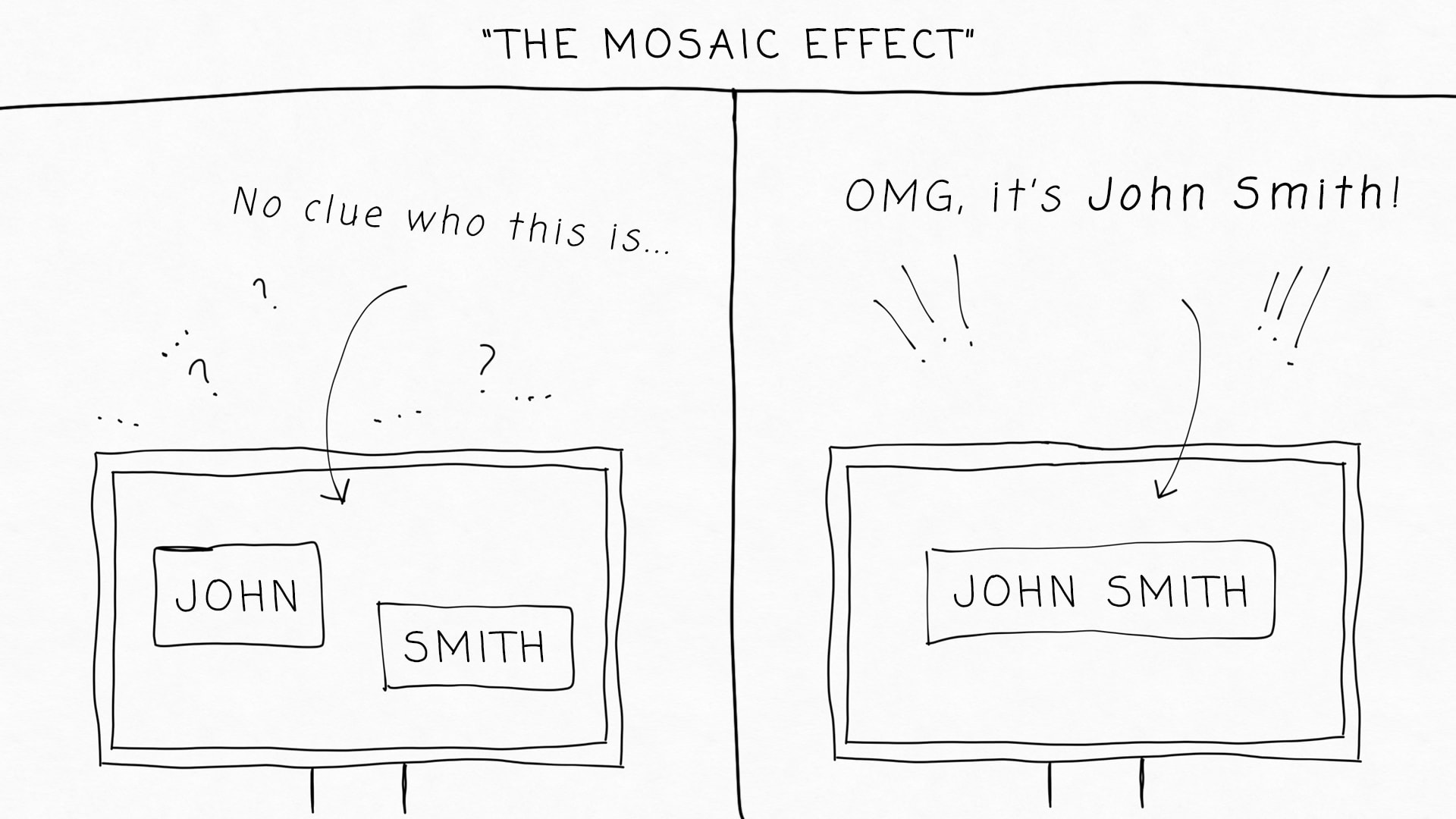
But here's an issue: even seemingly harmless information can become problematic when combined with other data points. Security experts call this the "mosaic effect" when separate pieces of information are assembled to reveal a complete picture. To better understand what this really means, it is best to perform a simply mental experiment.
Let us imagine the following situation: you see a painted text on a wall saying this:
7 11 96
What are your immediate thoughts on this? None, hopefully. This text does not deliver any significance, even though it is published and available in public. Now let's add a tiny bit of information to it, the wall now says this:
7 11 96 (7 - month, 11 - day, 96 - year)
After adding this tad of clue, one would now automatically think of this as a date - the wall's text has transformed from meaningless text into something shaped like a date. Continuing this mental experiment, let's say that now there is your name placed right above this date, the text is as follows:
John Smith
7 11 96 (7 - month, 11 - day, 96 - year)
A week passes. You now notice that the wall text has once again changed, and something else has been added:
John Smith
+1 (123) 456-7890
[email protected]
Uses Samsung Galaxy S22 (Android 12)
7 11 96 (7 - month, 11 - day, 96 - year)
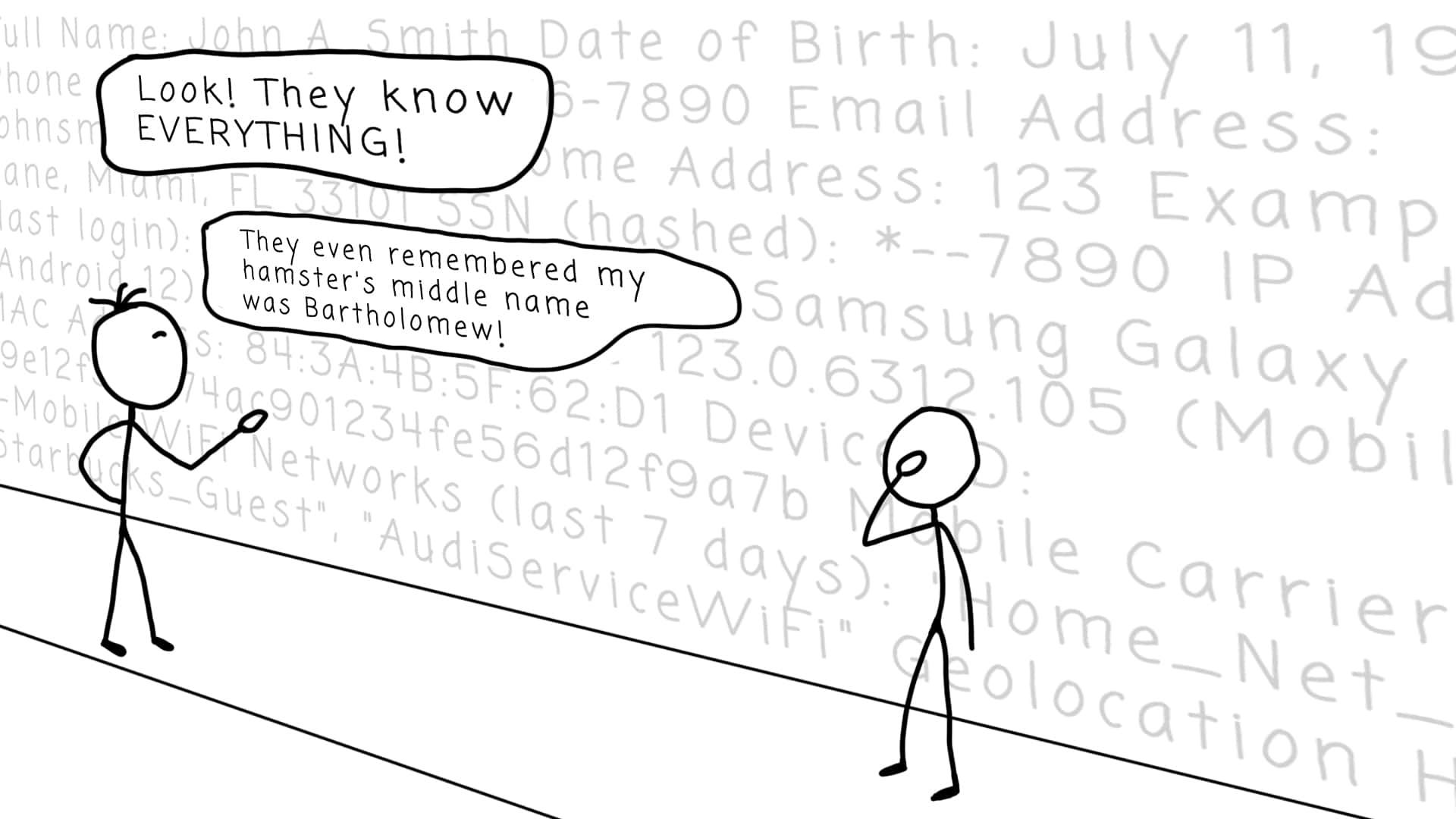
Another month passes. There is more and more text on the wall. The data becomes more organized and complete:
Full Name: John A. Smith
Date of Birth: July 11, 1996
Phone Number: +1 (123) 456-7890
Email Address: [email protected]
Home Address: 123 Example Lane, Miami, FL 33101
SSN (hashed): ***-**-7890
IP Address (last login): 173.128.78.25
Device: Samsung Galaxy S22 (Android 12)
Browser: Chrome 123.0.6312.105 (Mobile)
MAC Address: 84:3A:4B:5F:62:D1
Device ID: a9e12f3c8b74ac901234fe56d12f9a7b
Mobile Carrier: T-Mobile
WiFi Networks (last 7 days): "Home_Net_5G", "Starbucks_Guest", "AudiServiceWiFi"
Geolocation History: Frequent visits in/around Miami, FL; one trip to Orlando, FL (March 2025)
Current GPS Location: 25.7617° N, 80.1918° W
Voice Assistant History (Samsung Bixby):
- "Remind me to water the ferns at 9 AM"
- "Navigate to nearest Audi service center"
- "What's the best dairy-free pizza near me?"
Search History (Last 30 Days):
- "Best gardening gloves for sensitive skin"
- "Montessori vs traditional kindergarten"
- "Audi Q5 2020 brake replacement cost"
- "Dairy-free mozzarella brands"
- "Best gardening apps 2025"
Purchase History (Amazon):
- Gardena Hose Reel
- Organic seedling starter kit
- Montessori workbooks
App Usage (Daily Avg):
- Instagram: 1.2 hrs
- Google Maps: 20 mins
- WhatsApp: 40 mins
- MyAudi App: 10 mins
Biometric Data (stored via phone sensors):
- Fingerprint ID: registered
- Facial recognition: enabled
- Step count average: 4,800/day
Processed interests:
Shows interest in gardening equipment, kindergartens near Miami, Florida, getting Audi Q5 serviced, pizza with dairy-free cheese.
This is a rather oversimplified example - but it allows you to really understand how PII can be different - and it's not always as direct as your SSN, blood type, or passport number. Surely, your birth date alone might seem insignificant - but when combined with your name and address, it provides a lot more information for someone to potentially access your accounts or steal your identity. Context matters a lot with PII. Your name appearing in a phone book might not concern you, but that same name attached to sensitive health information or financial records becomes more problematic. The potential harm from exposed information depends not just on what information is revealed but how it could be used.
As digital footprints grow, the line between sensitive and non-sensitive information blurs. Information once considered harmless can become valuable for identity thieves and fraudsters who know how to connect the dots.
How Legislations Protect You
As threats to personal information have become more common, governments worldwide have responded with regulations designed to offer you protection - as well as give better control over your data and hold organizations accountable for protecting it.
The European Union's General Data Protection Regulation (GDPR) is a widely known standard. Covering anyone living in the EU or whose data is processed there, this regulation gives people substantial control over their personal information. Under GDPR, you have the right to access any data companies have collected about you, correct inaccurate information, and even request complete deletion - which is known as the famous "right to be forgotten." Companies must minimize the amount of data they collect, using only what's necessary for stated purposes. If you ever saw those privacy notices that pop up on websites, know that most of them exist because of GDPR requirements.
In the United States, there is the California Consumer Privacy Act (CCPA) and its expansion, the California Privacy Rights Act (CPRA), providing similar protections. California residents can find out what personal information businesses have collected about them, request deletion of that data, and opt out of having their information sold. When you see "Do Not Sell My Personal Information" links on websites, that's CCPA. Though only limited to California residents, these laws also often affect how companies handle everyone's data since it's easier to apply one standard across the website.
For health information, there is the Health Insurance Portability and Accountability Act (HIPAA), which provides specialized protection. This law aims to protect your medical records and other health information, requiring healthcare providers, insurance companies, and their business partners to implement specific security measures. That's also why your doctor asks you to sign acknowledgments about privacy practices.
All these regulations share common principles: transparency about data collection, limits on how information can be used, security requirements to prevent breaches, and individual rights regarding personal data. They also dictate proper destruction of PII when it's no longer needed. Those requirements for secure disposal explain why healthcare offices shred documents and why companies must properly erase digital files containing personal information.
Hidden Dangers of Your Personal Information
Despite strong regulations, personal information remains vulnerable in many everyday situations-often in ways people don't immediately recognize. Picture yourself working on a laptop at your favorite coffee shop. The free Wi-Fi is convenient, but it might not be secure. Without proper protection, others on the same network could potentially see information you're sending, including login credentials or personal details. That quick social media update from vacation? It not only tells friends about your trip but also broadcasts to potential thieves that your home is empty. And those fun quizzes that ask for your first pet's name or the street you grew up on? They're collecting common security question answers that could help someone access your accounts.
Even careful people can fall victim to phishing attempts. That urgent email appearing to come from your bank might actually be a convincing fake designed to capture your login information. The text message about a package delivery problem could lead to a website that steals your personal details.
Physical documents pose risks too. Tossing mail with your name and address into the recycling bin gives dumpster divers potential access to your information. But digital file disposal creates even more hidden dangers. When you delete files from your computer, you might think they're gone forever, but standard deletion is surprisingly ineffective at removing the actual data.
Think of standard file deletion like this: it's similar to tearing the index page out of a book but leaving all the content intact. The computer removes the reference to where the file is stored but leaves the actual information on your drive until it eventually gets overwritten with new data. With easily available recovery tools, someone with access to your device could potentially retrieve files you thought were gone forever.
This data persistence becomes particularly problematic when you sell your old computer, return a rental laptop, or dispose of a smartphone. Without proper data destruction, the next person who uses that device might have access to your personal files, photos, financial documents, or automatically saved passwords-even if you thought you deleted everything.
Protection Strategies
Protecting your personal information doesn't require technical expertise, just thoughtful habits and the right tools.
Passwords
Strong, unique passwords provide your first line of defense. Create different passwords for important accounts, especially financial ones, and make them complex enough to resist guessing. You should also have unique passwords for your most "important" accounts - for most people, this will be Google, Microsoft, and iCloud (Apple) - those accounts often save your other passwords, so you should definitely have completely unique passwords for them.
It's also important to note that by "unique", we really mean unique - not an added letter, digit, or symbol. So, "Password123" and "Password123!" are not considered unique - as the second password is simply a variation of the first. You need to create truly unique passwords, not variations, as they are easily guessed if your original password is leaked.
Surely, remembering all those passwords is not an easy task. The most obvious solution is to write down those passwords on a piece of paper - though, please, do not do this. Writing down your passwords on a piece of paper is a very insecure practice, and you should not do it.
Instead, you can and should use an external password manager to help generate and store these complex passwords securely, so you don't have to remember them all - this way, you only need to remember one strong password (to the password manager itself), and all other passwords will be managed by it. For crucial accounts, you should also enable two-factor authentication-this adds an extra verification step (usually a text message code, app notification, or a 2FA code) even if someone has your password.
Social Media
You should be mindful about what you share on social media. Check your privacy settings to control who sees your posts, and think twice before sharing identifying details like your full birth date, home address, or when you'll be away from home. Change your privacy settings to allow only Friends to view your posts - do you really want any person on Earth to see your birthday photos? Still, remember that even posts restricted to "friends only" can be screenshotted and shared elsewhere.

Settings
Take time to review privacy settings on your apps and online accounts. Almost every website or app has privacy settings, and by default most of them collect much more information than needed. Still, mainly due to laws and regulations, some may offer options to limit data collection if you look for them.
Phishing
Learn to recognize phishing attempts by watching for signs: urgent requests for personal information, slightly misspelled email addresses or website URLs, and messages that create pressure to act quickly without thinking. When in doubt, contact organizations directly through their official website rather than clicking links in messages. Additionally, you can search the websites or emails when in doubt, as they may often contain slight changes, even in a single character.
Information Disposal
Proper disposal of both physical and digital information is just as important as careful collection. Shred paper documents containing personal information instead of simply throwing them away. For digital files, remember that standard deletion doesn't effectively remove data-the information often remains recoverable. When disposing of old devices or storage media, or even when deleting sensitive files from your current computer, proper data destruction tools are essential for truly removing personal information.
How Organizations (should) Keep Your Information Safe
Responsible organizations protect your personal data through several important practices. They start with data minimization-collecting only what they truly need rather than gathering everything possible, which shows respect for your privacy and reduces risks if a breach occurs. They also classify different types of information based on sensitivity, applying stronger safeguards to sensitive data like credit card numbers than to basic information like newsletter preferences. Access controls limit who can see your data based on job requirements, while monitoring systems detect unusual patterns that might indicate misuse. Employee training is crucial since many data breaches begin with human error-regular security awareness training builds a stronger human defense against threats like malicious links and scams.
Organizations that handle your information responsibly also prepare for potential incidents before they happen. They develop clear procedures for responding to data breaches, including steps to contain damage, investigate incidents, notify affected individuals, and prevent future problems. Throughout the data lifecycle, proper destruction policies protect information that's no longer needed by securely shredding documents and properly erasing digital files when retention periods end. When evaluating organizations, examine their privacy policies and transparency reports, which reveal their approach to data protection. Above all, trustworthy organizations view protecting your information as an ongoing commitment rather than just a compliance exercise, helping you make informed choices about who to trust with your personal data.
Your data's journey
Personal information follows a predictable path from collection to disposal, and protection is needed at every stage. The lifecycle begins when you share information through forms, account creation, or purchases. Ethical collection involves clear consent-you should know what's being gathered and why. Ideally, organizations should only collect what's truly necessary for their stated purpose. Once collected, your information enters the storage phase, where it needs protection from both external threats like hackers and inappropriate internal access through measures such as encryption, access controls, and physical security. During the use stage, when your information is accessed for its intended purpose (verifying identity, processing transactions, or providing services), proper controls ensure it's used only for legitimate purposes by authorized people.
The sharing stage is particularly vulnerable, as your information moves between systems or organizations and needs protection in transit through secure transmission methods and clear agreements about protection and use. During the retention phase, responsible organizations set appropriate timeframes for keeping different types of data rather than storing information forever.
Finally, the often-overlooked destruction phase requires proper disposal of information that's reached the end of its useful life. For physical documents, this means shredding; for digital files, it requires secure deletion methods that truly remove the data. Once again, standard file deletion is comparable to removing a book from a library catalog while leaving the book on the shelf-the information remains available to anyone who knows how to look. Proper digital destruction overwrites data numerous times, ensuring it cannot be recovered even with specialized tools, completing the lifecycle and preventing old information from creating new privacy risks.
Why Hitting "Delete" Isn't Enough to Protect Your Personal Information
Most of us have a mental model of computer files that doesn't match reality. When you delete a file, you probably imagine it disappearing completely, like throwing paper into a shredder. The truth is very different-and understanding this difference is important for protecting your personal information.
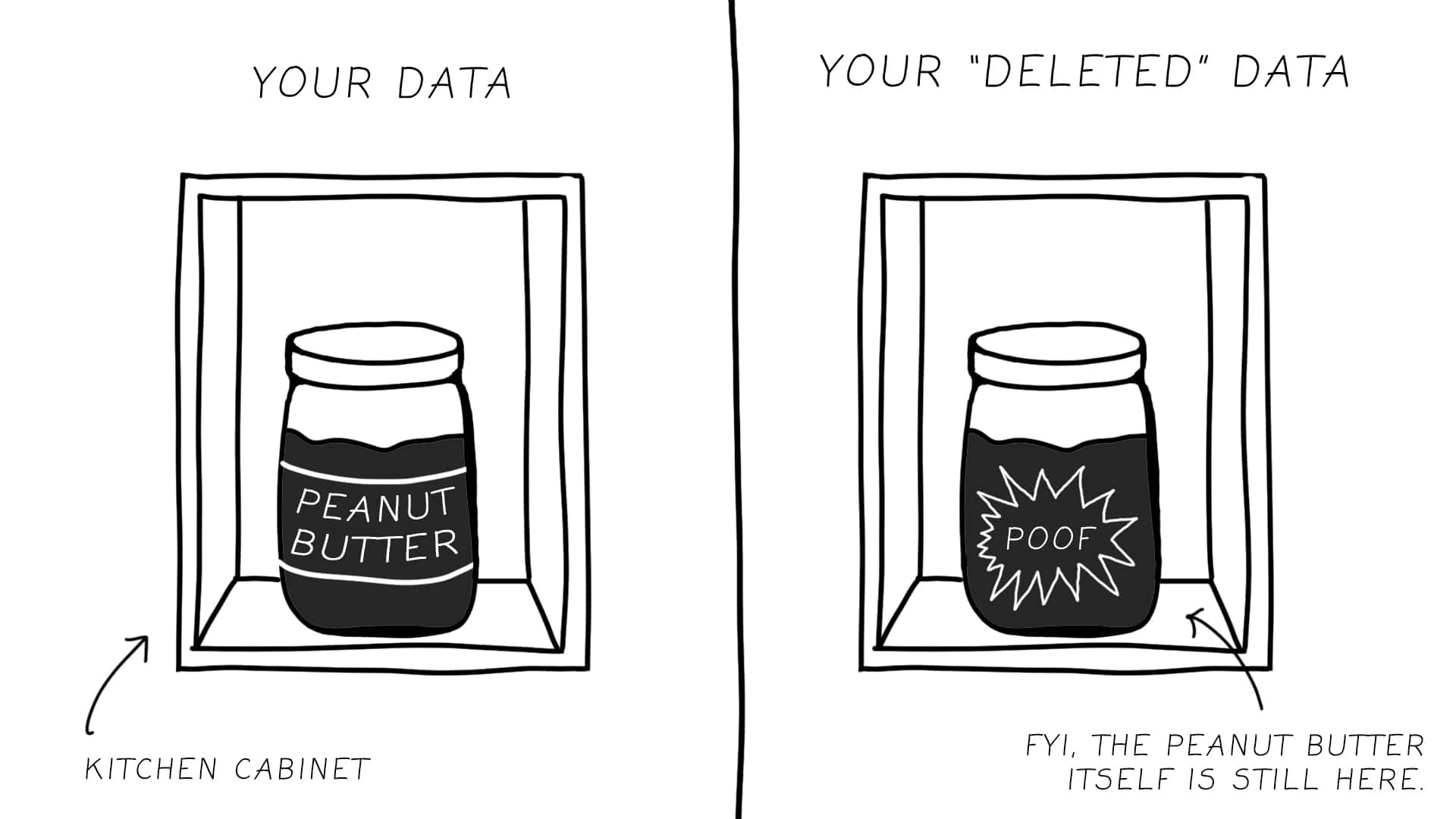
Here is an example that will help you understand standard file deletion: Let's imagine a peanut butter jar. It is sitting peacefully inside your kitchen cabinet. Then, suddenly, you want to get rid of the peanut butter jar. Here is what you do next: you open the kitchen cabinet, find the jar, and finally... rip off the jar's label and packaging. Now you have a jar full of peanut butter, still in your cabinet - but without its label. This is exactly what "standard" file deletion is on your computer.
When you delete a file, your computer removes the reference to where that file is stored on your hard drive, but the actual content remains untouched-just like removing the jar's label, but not throwing out the jar itself. The space that your file content was taking is marked as "available for new data", but until it's actually overwritten with something else, the original information remains physically present on your storage device. Think of it as you continuing to place stuff into your kitchen cabinet, until there is no more space in it, and you finally throw out the jar.
This creates a significant privacy risk. With freely available data recovery tools-some even free-someone with access to your device could potentially recover files you thought were permanently deleted. These tools scan storage media for data that no longer appears in the file system but still exists physically on the device - just like opening your kitchen cabinet and finding a jar of peanut butter with no label on it-while it is slightly more challenging, it is still very easily accomplishable.
The implications become clear in common scenarios: selling or donating an old computer without properly erasing the hard drive/SSD could give the next owner access to your personal documents, financial records, photos, and credit card data. Returning a rental laptop without secure deletion might expose confidential work documents. Disposing of an old smartphone could put your personal messages and account information at risk. Even discarding a USB drive or external hard drive without proper erasure leaves your data vulnerable.
The risk extends to everyday file management too. When you delete sensitive documents from a shared computer or network drive, standard deletion doesn't provide adequate protection against others accessing that information later. Simply emptying the Recycle Bin or Trash folder doesn't truly remove the data from your storage device.
This persistent data problem affects organizations too. Companies that fail to properly destroy customer information when no longer needed risk violating privacy regulations and exposing sensitive data. Healthcare providers, financial institutions, and other organizations handling regulated data have specific obligations to ensure complete destruction of information-obligations that standard deletion doesn't fulfill.
Beyond Deletion: How Secure File Shredding Protects Your Digital Privacy
Just as you wouldn't throw sensitive paper documents in the trash without shredding them first, digital files containing personal information need proper destruction beyond standard deletion. This is where secure file shredding becomes essential.
Secure file shredding is a process that overwrites the actual data content multiple times with random patterns, making the original information unrecoverable even with specialized forensic tools. Unlike standard deletion, which leaves the content intact and recoverable, proper digital shredding permanently removes all traces of the information.
When would you need this level of protection? Consider these common situations: Before selling, donating, or recycling computers, tablets, or smartphones, secure file shredding prevents the next user from accessing your personal information. When returning leased equipment like rental computers or copiers with internal storage, it ensures your data doesn't travel with the device. After working with sensitive files on public or shared computers, it removes all traces of your information. Following data breaches or malware infections, secure shredding can eliminate potentially compromised files containing personal information.
Secure file shredding is also important for regulatory compliance. Privacy laws like GDPR explicitly require proper data destruction when information is no longer needed or when individuals request deletion of their personal data. For businesses, government agencies, healthcare providers, and financial institutions, demonstrating and meeting compliant destruction of sensitive information has become a legal necessity rather than just a best practice.
The process works by overwriting the physical location on the storage device where the file was stored. By writing new random data over that location multiple times (using various patterns designed to eliminate any residual data), secure shredding tools ensure the original information cannot be reconstructed. The most popular standards, like the U.S. Department of Defense 5220.22-M method, specify multiple overwrite passes with verification to guarantee complete destruction.
Unlike physical document shredding, which requires dedicated hardware, digital file shredding is accomplished through specialized software. These tools range from basic programs that securely delete individual files to comprehensive solutions that can wipe entire drives, erase free space where deleted files might linger, and provide verification certificates documenting the destruction process.
For individuals and organizations concerned about privacy, secure file shredding provides peace of mind that sensitive personal information truly disappears when deleted. In a world where data breaches and identity theft continue to rise, this added layer of protection has become increasingly valuable.
Offigneum: Your Solution for Comprehensive Digital File Protection
As we've seen throughout this guide, protecting personally identifiable information requires attention at every stage-especially when that information reaches the end of its useful life. For those serious about privacy protection, Offigneum file shredding software offers a comprehensive solution to the challenges of secure digital destruction. Offigneum goes beyond standard deletion by implementing military-grade overwriting techniques that make recovered data impossible. When you need absolute certainty that sensitive files are truly gone, this professional-grade solution provides multiple security standards to meet various requirements-from basic personal privacy to strict regulatory compliance.
The software works across various storage media, including internal hard drives, external storage devices, USB drives, and network storage. This flexibility means you can apply the same thorough destruction process regardless of where sensitive information is stored.
Offigneum's batch processing capabilities make it practical for both individual and organizational use. You can securely destroy a single sensitive document or process hundreds of thousands of files at once, making it suitable for everything from personal privacy protection to large-scale data disposal projects.
You can learn more about Offigneum (software for Windows) on this website. Additionally, MacGlacio offers the same features and benefits as Offigneum while focusing specifically on Macs. You can learn more about MacGlacio (software for macOS) on this website.
Protecting privacy isn’t just about handling data carefully while it’s being used-it also means knowing when and how to let it go. True privacy requires attention at every stage of the data lifecycle, especially when it’s time to securely destroy information that's no longer needed. As more people become aware of the importance of data privacy, tools like Offigneum and MacGlacio are helping both individuals and organizations take back control-even when it comes to how their information is erased for good.
Learn more about Offigneum and the full list of its features on its official website:
www.ambeteco.com/Offigneum/
Legal Disclaimer: The information provided in this article is for general informational purposes only and does not constitute legal or technical advice. The methods and tools described, including Offigneum file-shredding software, are intended to enhance data security and privacy. However, no data erasure method can guarantee absolute protection against data recovery, due to many factors, including user error, improper handling of storage media, and external environmental influences. Users should exercise caution and consult a professional if unsure about data deletion processes. Offigneum and its developers disclaim any liability for damages or losses arising from the use or inability to use the described tools or techniques or instructions. For specific legal and technical concerns, please seek appropriate professional guidance.







